```html
Understanding the Use of Public Keys in Blockchain Technology
Blockchain technology has revolutionized various industries by providing decentralized and secure solutions for data management and transactions. At the heart of blockchain lies the concept of public key cryptography, which ensures the security and authenticity of transactions. Let's delve deeper into how public keys are utilized in blockchain systems and their significance.
Public keys are a fundamental component of asymmetric cryptography, a cryptographic system that uses pairs of keys: public keys and private keys. In this system, the public key is freely distributed and used to encrypt data, while the corresponding private key is kept secret and used to decrypt the data.
In the context of blockchain, public keys play several crucial roles:
Authentication:
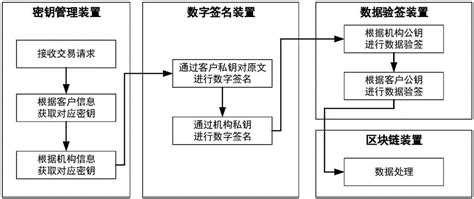
Public keys are used to verify the identity of participants in a blockchain network. Each participant has a unique pair of public and private keys. When a user initiates a transaction, they sign it with their private key, and other participants can verify the authenticity of the transaction using the sender's public key.
Encryption:
Public keys are also used to encrypt sensitive information, such as wallet addresses or transaction data, ensuring that only the intended recipient, who possesses the corresponding private key, can access the information.
Address Generation:
In many blockchain networks, public keys are used to generate unique addresses for participants. These addresses serve as identifiers for sending and receiving assets on the blockchain.
When a transaction is initiated on a blockchain network:
The use of public key cryptography enhances the security and trustworthiness of blockchain networks in several ways:
- Immutable Transactions: Transactions cannot be altered or tampered with once they are added to the blockchain, as changing the data would require altering the corresponding digital signatures, which is practically impossible without the private key.
- Transparent Verification: Public keys allow for transparent verification of transactions by anyone on the network, promoting trust and accountability.
- Decentralization: Asymmetric cryptography enables secure peertopeer transactions without the need for centralized authorities, fostering decentralization and resilience against attacks.
Effective management of public keys is essential to maintain the security of blockchain networks:
- Secure Storage: Private keys must be stored securely to prevent unauthorized access. Hardware wallets and cold storage solutions offer robust protection against theft and hacking.
- Key Rotation: Regularly rotating keys reduces the risk of compromise. Participants should generate new key pairs periodically and update their public keys accordingly.
- Key Revocation: In the event of a key compromise, mechanisms for key revocation and replacement should be in place to mitigate potential risks.
Public keys form the foundation of trust and security in blockchain technology, enabling secure transactions, identity verification, and data encryption. By understanding the role of public key cryptography and implementing best practices for key management, blockchain participants can harness the full potential of this transformative technology while safeguarding their assets and data.

